(add text) |
|||
| Line 41: | Line 41: | ||
'''Overview of DES Algorithm''' | '''Overview of DES Algorithm''' | ||
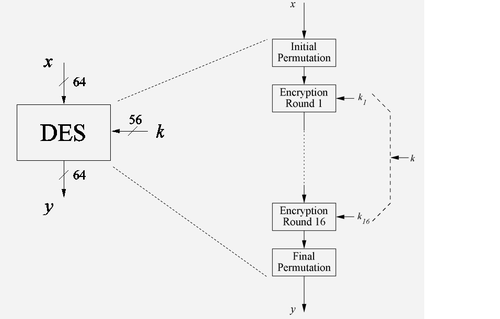
| − | [[File:DES_Overview.png|500px|thumb|left|Fig 1:Overview of the DES Algorithm]] | + | [[File:DES_Overview.png|500px|thumb|left|Fig 1: Overview of the DES Algorithm]] |
* DES is a Symmetric cipher: uses same key for encryption and decryption | * DES is a Symmetric cipher: uses same key for encryption and decryption | ||
| Line 55: | Line 55: | ||
* The IP has no effect on the DES security at all. | * The IP has no effect on the DES security at all. | ||
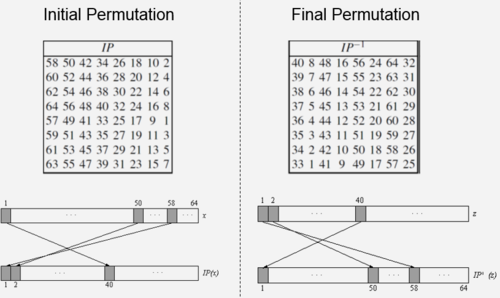
| − | [[File:IPFP.png|500px|thumb|left|Fig 2:Initial Permutation(left) and the Final Permutation(right) tables ]] | + | [[File:IPFP.png|500px|thumb|left|Fig 2: Initial Permutation(left) and the Final Permutation(right) tables ]] |
2. DES Encryption Round - Feistel Networks | 2. DES Encryption Round - Feistel Networks | ||
| Line 62: | Line 62: | ||
* Advantage: encryption and decryption differ only in keyschedule( explained later ) | * Advantage: encryption and decryption differ only in keyschedule( explained later ) | ||
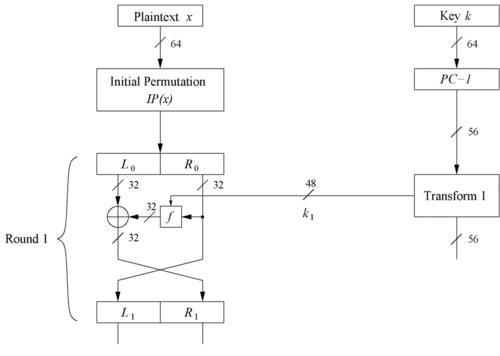
| − | [[File:FN.png|500px|thumb|left|Fig 3: Encryption | + | [[File:FN.png|500px|thumb|left|Fig 3: Encryption block round 1 - Feistel Networks]] |
| − | * The encryption block takes an input of 64 bit data permuted in the IP | + | * The encryption block for round 1 in Fig 3 takes an input of 64 bit data permuted in the IP |
* Plaintext is split into 32-bit halves <math>L_i</math> and <math>R_i</math> | * Plaintext is split into 32-bit halves <math>L_i</math> and <math>R_i</math> | ||
* <math>R_i</math> is fed into the '''function f''', the output of which is then XORed with <math>L_i</math> | * <math>R_i</math> is fed into the '''function f''', the output of which is then XORed with <math>L_i</math> | ||
| Line 71: | Line 71: | ||
<math>L_i = R_{i-1}</math> | <math>L_i = R_{i-1}</math> | ||
| + | |||
<math>R_i = L_{i-1} \oplus f(R_{i-1},k_i)</math> | <math>R_i = L_{i-1} \oplus f(R_{i-1},k_i)</math> | ||
| + | |||
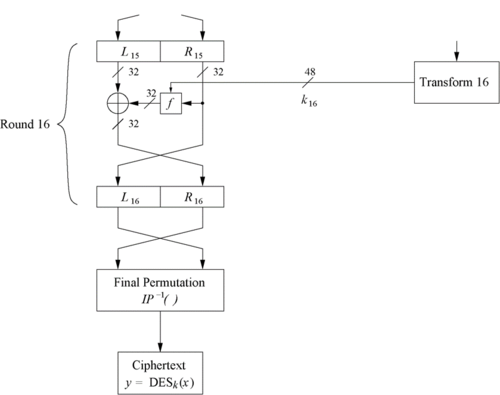
| + | [[File:FNfinal.png|500px|thumb|left|Fig 4: Encryption block final round - Feistel Networks]] | ||
| + | |||
| + | * And as seen in Fig 1, we have sixteen such rounds. | ||
| + | * And the Left and Right side bits are swapped again before the Final Permutation(FP) as shown in Fig 4. | ||
| + | |||
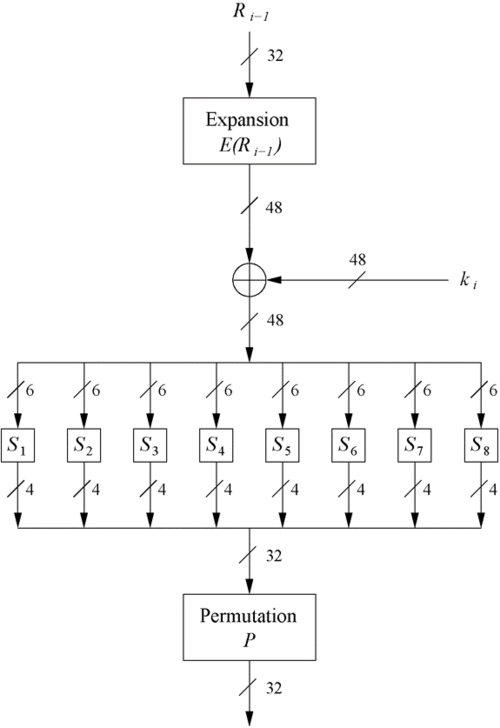
| + | 3. The f-funtion(inside the feistel network) | ||
| + | |||
| + | [[File:f_fucntion.png|500px|thumb|left|Fig 5: The f-function block]] | ||
| + | |||
| + | * Main operation of DES | ||
| + | * Inputs to f function are <math>R_{i-1}</math> and round key <math>k_i</math> | ||
| + | * It has 4 main steps in Fig 5 : | ||
| + | # Expansion block E | ||
| + | # XOR with round key | ||
| + | # S-box substitution (eight of them) | ||
| + | # Permutaion | ||
Revision as of 08:58, 11 June 2015
Data Encryption Standard(DES)
A slecture on Cryptography by student Divya Agarwal and Katie Marsh
Partly based on the Summer 2015 lecture material of Prof. Paar.
Contents
Link to video on youtube
Accompanying Lecture Notes
Introduction
- DES is a block cipher and as the name suggests it works on blocks of bits or binary numbers--the 0s and the 1s common to digital world. It encrypts group of 64 plaintext bits(one block) and returns 64 ciphertext bits. To do the encryption, DES uses keys which are also 64 bits long. However, every 8th key bit is ignored in the DES algorithm, so that the effective key size is 56 bits.
Block Cipher Primitives
- Confusion : An encryption operation where the relationship between plaintext and ciphertext is obscured. Today, a common element for achieving confusion is substitution, which is found in both AES and DES.
- Diffusion : An encryption operation where the influence of one plaintext symbol is spread over many ciphertext symbols with the goal of hiding statistical properties of the plaintext. A simple diffusion element is the bit permutation, which is frequently used within DES.
Both operations by themselves cannot provide security. The idea is to concatenate confusion and diffusion elements to build a more secure cipher.
Overview of DES Algorithm
- DES is a Symmetric cipher: uses same key for encryption and decryption
- Uses 16 rounds which all perform the identical operation
- Different subkey(48 bit) in each round derived from main key
Internal structure of DES
1. Initial Permutaion(IP) : This is the first thing that is seen in the expanded view of DES block in Fig 1.
- IP is a bitwise permutation or simple crosswiring in hardware.
- The corsswiring is done according to the table(left) given in Fig 2.
- The IP has no effect on the DES security at all.
2. DES Encryption Round - Feistel Networks
- DES structure is a Feistel network
- Advantage: encryption and decryption differ only in keyschedule( explained later )
- The encryption block for round 1 in Fig 3 takes an input of 64 bit data permuted in the IP
- Plaintext is split into 32-bit halves $ L_i $ and $ R_i $
- $ R_i $ is fed into the function f, the output of which is then XORed with $ L_i $
- Left and right half halves are swapped at the end of one encryption round
- Each encryption round can be expressed as :
$ L_i = R_{i-1} $
$ R_i = L_{i-1} \oplus f(R_{i-1},k_i) $
- And as seen in Fig 1, we have sixteen such rounds.
- And the Left and Right side bits are swapped again before the Final Permutation(FP) as shown in Fig 4.
3. The f-funtion(inside the feistel network)
- Main operation of DES
- Inputs to f function are $ R_{i-1} $ and round key $ k_i $
- It has 4 main steps in Fig 5 :
# Expansion block E # XOR with round key # S-box substitution (eight of them) # Permutaion
References
- C. Paar. Understanding Cryptography. Lecture Notes. Dept. of Electr. Eng. and Information Sciences, Ruhr University.
- C. Paar and J. Pelzl. Understanding Cryptography. A textbook for Student and Practitioners. Springer 2010.
Questions and comments
If you have any questions, comments, etc. please post them here.