(added page) |
|||
| Line 1: | Line 1: | ||
| − | [[Category:2015 Summer | + | [[Category:2015 Summer Cryptography Paar]] |
| − | [[Category:]] | + | [[Category:Cryptography]] |
| − | [[Category:]] | + | [[Category:Paar]] |
[[Category:slecture]] | [[Category:slecture]] | ||
| − | <center><font size= | + | <center><font size= 6>DES - Decryption</font size> |
| − | A [http://www.projectrhea.org/learning/slectures.php slecture] by | + | A [http://www.projectrhea.org/learning/slectures.php slecture] on Cryptography by student Divya Agarwal and Katie Marsh. |
Partly based on the [[2015 Summer Cryptography Paar| Summer 2015]] lecture material of Paar. | Partly based on the [[2015 Summer Cryptography Paar| Summer 2015]] lecture material of Paar. | ||
</center> | </center> | ||
---- | ---- | ||
| − | + | ==Decryption - Theory== | |
| − | == | + | |
| − | + | ||
| − | + | ||
| − | + | DES as discussed is based on Feistel networks. And in Feistel ciphers only the '''keyschedule''' has to be modified for '''decryption'''. | |
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | Step 1: Generate the same 16 round keys in reverse order for decryption, that is given initial key <math>k</math> can we get <math>k_{16}</math> and the rest. | |
| − | + | ||
| − | + | ||
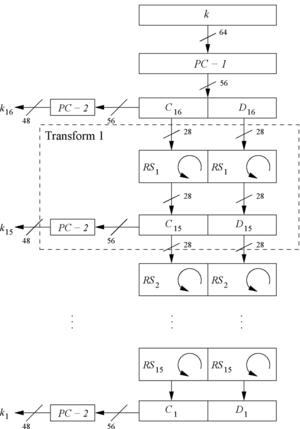
| − | + | Step 2: As D0=D16 and C0=C16 the first round key can be generated by applying PC-2 right after PC-1 (no rotation here!). Refer Fig 1 for more details. | |
| + | [[File:RevKS.png|300px|thumb|left|Fig 1: Reversed key Schedule for DES]] | ||
| + | |||
| + | Step 3: All other rotations of C and D can be reversed to reproduce the other round keys resulting in: | ||
| + | * No rotation in round 1. | ||
| + | * One bit rotation to the '''right''' in rounds 2, 9 and 16. | ||
| + | * Two bit rotations to the '''right''' in all other rounds. | ||
| + | |||
| + | Step 4: Note, the decryption and encryption function are the same essentially. | ||
| + | |||
| + | The complete lecture by Prof. Paar can be found [https://www.youtube.com/watch?v=l-7YW06BFNs here]. | ||
| + | |||
| + | == References== | ||
| + | * C. Paar. Understanding Cryptography. Lecture Notes. Dept. of Electr. Eng. and Information Sciences, Ruhr University. | ||
| + | * C. Paar and J. Pelzl. Understanding Cryptography. A textbook for Student and Practitioners. Springer 2010. | ||
---- | ---- | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
==[[2015_Summer_Paar_DES - Decryption_Divya Agarwal and Katie Marsh_comments | Questions and comments]]== | ==[[2015_Summer_Paar_DES - Decryption_Divya Agarwal and Katie Marsh_comments | Questions and comments]]== | ||
If you have any questions, comments, etc. please post them [[2015_Summer_Paar_DES - Decryption_Divya Agarwal and Katie Marsh_comments|here]]. | If you have any questions, comments, etc. please post them [[2015_Summer_Paar_DES - Decryption_Divya Agarwal and Katie Marsh_comments|here]]. | ||
Latest revision as of 07:26, 18 June 2015
A slecture on Cryptography by student Divya Agarwal and Katie Marsh.
Partly based on the Summer 2015 lecture material of Paar.
Decryption - Theory
DES as discussed is based on Feistel networks. And in Feistel ciphers only the keyschedule has to be modified for decryption.
Step 1: Generate the same 16 round keys in reverse order for decryption, that is given initial key $ k $ can we get $ k_{16} $ and the rest.
Step 2: As D0=D16 and C0=C16 the first round key can be generated by applying PC-2 right after PC-1 (no rotation here!). Refer Fig 1 for more details.
Step 3: All other rotations of C and D can be reversed to reproduce the other round keys resulting in:
* No rotation in round 1. * One bit rotation to the right in rounds 2, 9 and 16. * Two bit rotations to the right in all other rounds.
Step 4: Note, the decryption and encryption function are the same essentially.
The complete lecture by Prof. Paar can be found here.
References
- C. Paar. Understanding Cryptography. Lecture Notes. Dept. of Electr. Eng. and Information Sciences, Ruhr University.
- C. Paar and J. Pelzl. Understanding Cryptography. A textbook for Student and Practitioners. Springer 2010.
Questions and comments
If you have any questions, comments, etc. please post them here.