(Added youtube links) |
|||
| (5 intermediate revisions by the same user not shown) | |||
| Line 1: | Line 1: | ||
[[Category:2015 Summer Cryptography Prof. Paar]] | [[Category:2015 Summer Cryptography Prof. Paar]] | ||
| − | [[Category: | + | [[Category:Paar]] |
[[Category:Cryptography]] | [[Category:Cryptography]] | ||
[[Category:slecture]] | [[Category:slecture]] | ||
| Line 6: | Line 6: | ||
<center><font size=6> | <center><font size=6> | ||
| − | + | DES Key Schedule | |
</font size> | </font size> | ||
| − | A [http://www.projectrhea.org/learning/slectures.php slecture] | + | A [http://www.projectrhea.org/learning/slectures.php slecture] on [[Cryptography]] by student Divya Agarwal and Katie Marsh. |
| − | Partly based on the [[2015 Summer Cryptography Paar|Cryptography Summer 2015]] lecture material of | + | Partly based on the [[2015 Summer Cryptography Paar|Cryptography Summer 2015]] lecture material of Prof. Paar. |
</center> | </center> | ||
---- | ---- | ||
---- | ---- | ||
| − | + | Introduction to Key Schedule by Prof. Paar. | |
| − | + | ||
| + | =[https://youtu.be/GGtKeWizkaY Link to video on youtube]= | ||
| + | <youtube>https://youtu.be/GGtKeWizkaY</youtube> | ||
---- | ---- | ||
| + | ''' | ||
| + | == Accompanying Lecture Notes == | ||
| + | ''' | ||
---- | ---- | ||
| + | |||
| + | ==== DES Key Schedule - Theory ==== | ||
| + | |||
| + | The DES ''key schedule'' genrates 16 round keys (or sub-keys) for the 16 encryption rounds. The sub-keys are derived out of the original 64-bit key given as an input. | ||
| + | |||
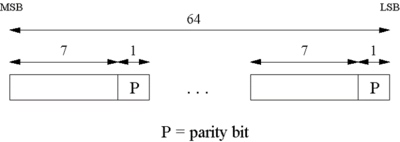
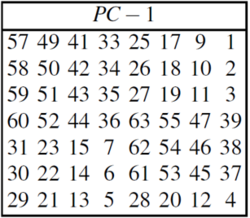
| + | Step 1: The original 64-bit key is reduced to 56-bit key using the PC-1 permutation table (Fig 1a). Note: Every 8th bit is ignored in the table(i.e. bits numbered 8, 16, 24, 32, 40, 48, 56, and 64). Nevertheless number the bits from 1 to 64, going left to right(Fig 1b). | ||
| + | |||
| + | [[File:KS2.png|400px|thumb|left|Fig 1a: PC-1 Permutation table]] | ||
| + | [[File:KS1.png|250px|thumb|left|Fig 1b: 64-bit key input bit description]] | ||
| + | |||
| + | =[http://youtu.be/H10mlpjjLAQ Link to video on youtube]= | ||
| + | <youtube>http://youtu.be/H10mlpjjLAQ</youtube> | ||
| + | |||
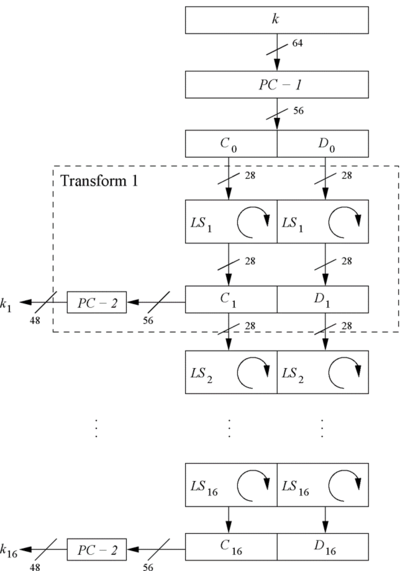
| + | Step 2: Split the 56-bit Key in two 28-bit halves: Left - <math>C_0</math> and Right - <math>D_0</math>(Refer Fig 2). | ||
| + | |||
| + | [[File:KS3.png|400px|thumb|left|Fig 2: Key Schedule for DES encryption]] | ||
| + | |||
| + | =[http://youtu.be/sI1FoqiXix0 Link to video on youtube]= | ||
| + | <youtube>http://youtu.be/sI1FoqiXix0</youtube> | ||
| + | |||
| + | Step 3: With <math>C_0</math> and <math>D_0</math> defined, we now create sixteen blocks <math>C_n</math> and <math>D_n</math>, <math>1≤n≤16</math> using following rules. | ||
| + | * In rounds i = 1,2,9,16 , the two halves are each rotated left by '''one''' bit. | ||
| + | * In all other rounds, where i ≠ 1,2,9,16 , the two halves are each rotated left by '''two''' bits. | ||
| + | * Total number of rotations 4*1 + 12* 2 = 28 which leads to an interesting property : <math>C_0</math>=<math>C_{16}</math> and <math>D_0</math>=<math>D_{16}</math>. | ||
| + | |||
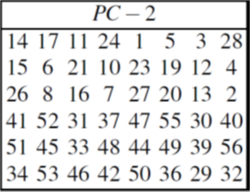
| + | Step 4: We now form the keys <math>K_n</math>, for <math>1≤n≤16</math>, by applying the PC-2 permutation table (Fig 3) to each of the concatenated pairs <math>C_nD_n</math> to generate 48-bit keys out of 56-bit bit <math>C_nD_n</math>. | ||
| + | |||
| + | [[File:KS4.png|250px|thumb|left|Fig 3: PC-2 Permutation table]] | ||
| + | |||
| + | The complete lecture video can be found [https://www.youtube.com/watch?v=l-7YW06BFNs here]. | ||
| + | |||
| + | ==== DES Key Schedule - Example ==== | ||
| + | |||
| + | |||
| + | |||
| + | |||
| + | ---- | ||
| + | == References== | ||
| + | * C. Paar. Understanding Cryptography. Lecture Notes. Dept. of Electr. Eng. and Information Sciences, Ruhr University. | ||
| + | * C. Paar and J. Pelzl. Understanding Cryptography. A textbook for Student and Practitioners. Springer 2010. | ||
| + | * J. Orlin Grabbe, The DES Algorithm Illustrated. | ||
| + | ---- | ||
| + | |||
==[[2015_Summer_Cryptography_Prof. Paar_Introduction to Cryptography_Divya Agarwal and Katie Marsh_comments | Questions and comments]]== | ==[[2015_Summer_Cryptography_Prof. Paar_Introduction to Cryptography_Divya Agarwal and Katie Marsh_comments | Questions and comments]]== | ||
If you have any questions, comments, etc. please post them [[2015_Summer_Cryptography_Prof. Paar_Introduction to Cryptography_Divya Agarwal and Katie Marsh_comments|here]]. | If you have any questions, comments, etc. please post them [[2015_Summer_Cryptography_Prof. Paar_Introduction to Cryptography_Divya Agarwal and Katie Marsh_comments|here]]. | ||
Latest revision as of 05:33, 18 June 2015
DES Key Schedule
A slecture on Cryptography by student Divya Agarwal and Katie Marsh.
Partly based on the Cryptography Summer 2015 lecture material of Prof. Paar.
Introduction to Key Schedule by Prof. Paar.
Contents
Link to video on youtube
Accompanying Lecture Notes
DES Key Schedule - Theory
The DES key schedule genrates 16 round keys (or sub-keys) for the 16 encryption rounds. The sub-keys are derived out of the original 64-bit key given as an input.
Step 1: The original 64-bit key is reduced to 56-bit key using the PC-1 permutation table (Fig 1a). Note: Every 8th bit is ignored in the table(i.e. bits numbered 8, 16, 24, 32, 40, 48, 56, and 64). Nevertheless number the bits from 1 to 64, going left to right(Fig 1b).
Link to video on youtube
Step 2: Split the 56-bit Key in two 28-bit halves: Left - $ C_0 $ and Right - $ D_0 $(Refer Fig 2).
Link to video on youtube
Step 3: With $ C_0 $ and $ D_0 $ defined, we now create sixteen blocks $ C_n $ and $ D_n $, $ 1≤n≤16 $ using following rules.
- In rounds i = 1,2,9,16 , the two halves are each rotated left by one bit.
- In all other rounds, where i ≠ 1,2,9,16 , the two halves are each rotated left by two bits.
- Total number of rotations 4*1 + 12* 2 = 28 which leads to an interesting property : $ C_0 $=$ C_{16} $ and $ D_0 $=$ D_{16} $.
Step 4: We now form the keys $ K_n $, for $ 1≤n≤16 $, by applying the PC-2 permutation table (Fig 3) to each of the concatenated pairs $ C_nD_n $ to generate 48-bit keys out of 56-bit bit $ C_nD_n $.
The complete lecture video can be found here.
DES Key Schedule - Example
References
- C. Paar. Understanding Cryptography. Lecture Notes. Dept. of Electr. Eng. and Information Sciences, Ruhr University.
- C. Paar and J. Pelzl. Understanding Cryptography. A textbook for Student and Practitioners. Springer 2010.
- J. Orlin Grabbe, The DES Algorithm Illustrated.
Questions and comments
If you have any questions, comments, etc. please post them here.
Back to 2015 Summer Cryptography Prof. Paar