A slecture on Cryptography by student Divya Agarwal and Katie Marsh (or anonymous if desired)
Partly based on the Cryptography Summer 2015 lecture material of Paar.
Contents
1. Introduction to cryptography
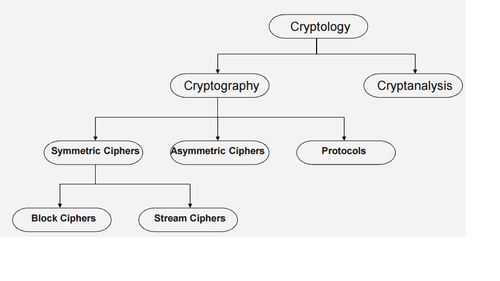
The block diagram below shows an overview of the field of cryptology.
Cryptography is the science of secret writing with the goal to hide the orginal message.
Cryptanalysis is the science and sometimes art of breaking cryptosystems.
Cryptography itself splits into three main branches:
1. Symmetric Algorithms :
- Also known as private-key, single-key or secret-key cryptography
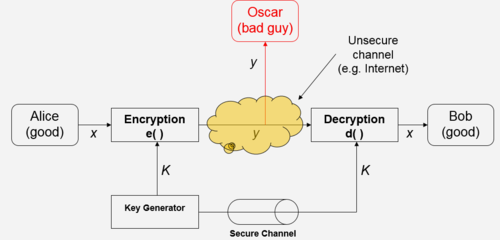
- In Fig 2, x is the plaintext message which Alice wants to send, y is the ciphertext message which has been encrypted, K is the key to encrypt or decrypt the message.
- Encryption equation : $ y = e_k(x) $ , where $ e_k(x) $ is the encryption function
Decryption equation : $ x = d_k(y) $ , where $ d_k(x) $ is the decryption function
- Encryption and decryption are inverse operations if the same key K is used on both sides :
$ d_k(y)= d_k(e_k(x))= x $
- However, the system is only secure if an attacker does not learn the key K!
2.
Text of first section goes here. Here is an example of an equation.
$ f(x)= \frac{1}{5} \sin x \int_{-\infty}^\alpha \pi^y dy $
2. Derivation (Replace by appropriate section title)
Text of second section goes here. Here is an example of a list
- Blah
- Blih
- Bloh
- Blouh
4. Conclusion (Replace by appropriate section title)
Text of fourth section goes here.
5. References
- C. Paar. Understanding Cryptography. Lecture Notes. Dept. of Electr. Eng. and Information Sciences, Ruhr University.
- C. Paar and J. Pelzl. Understanding Cryptography. A textbook for Student and Practitioners. Springer 2010.
Questions and comments
If you have any questions, comments, etc. please post them here.
Back to 2015 Summer Cryptography Paar