| Line 24: | Line 24: | ||
====Overview of AES==== | ====Overview of AES==== | ||
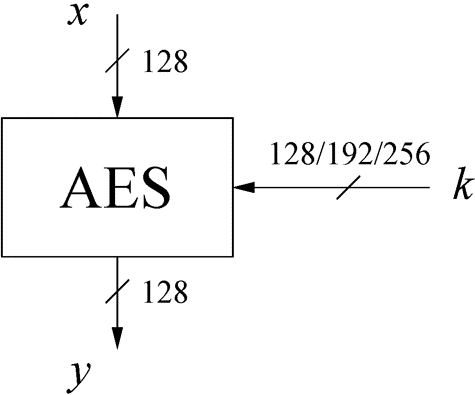
*AES is a block cipher | *AES is a block cipher | ||
| − | *information is handled 128 bits at a time | + | *information is handled 128 bits at a time, divided into 16 bytes. |
*key can be 128, 192, or 256 bits long | *key can be 128, 192, or 256 bits long | ||
| Line 48: | Line 48: | ||
====Layers==== | ====Layers==== | ||
| + | *Byte Substitution Layer (S) | ||
| + | This layer consists of 16 identical S-box which take in 8 bits and output 8 bits. Let <math> A_i </math> be one byte of input. Then <math> S(A_i)=B_i </math> | ||
| + | But what is the function S? First, the <math> A_i^{-1} \in GF(2^8) </math> is calculated. Then, an affine transformation is applied. | ||
| + | |||
| + | |||
| + | In software, S-boxes are usually a look up table. | ||
---- | ---- | ||
---- | ---- | ||
| + | |||
| + | ==References== | ||
| + | |||
==[[2015_Summer_Cryptography_Paar_Internal Structure of AES_Katie Marsh and Divya Agarwal_comments | Questions and comments]]== | ==[[2015_Summer_Cryptography_Paar_Internal Structure of AES_Katie Marsh and Divya Agarwal_comments | Questions and comments]]== | ||
If you have any questions, comments, etc. please post them [[2015_Summer_Cryptography_Paar_Internal Structure of AES_Katie Marsh and Divya Agarwal_comments|here]]. | If you have any questions, comments, etc. please post them [[2015_Summer_Cryptography_Paar_Internal Structure of AES_Katie Marsh and Divya Agarwal_comments|here]]. | ||
Revision as of 08:21, 18 June 2015
Internal Structure of AES
A slecture by students Katie Marsh and Divya Agarwal
Based on the Cryptography lecture material of Prof. Paar.
Contents
Link to video on youtube
Accompanying Notes
Overview of AES
- AES is a block cipher
- information is handled 128 bits at a time, divided into 16 bytes.
- key can be 128, 192, or 256 bits long
- number of rounds depends on the key length (can be 10/12/14 rounds respectively)
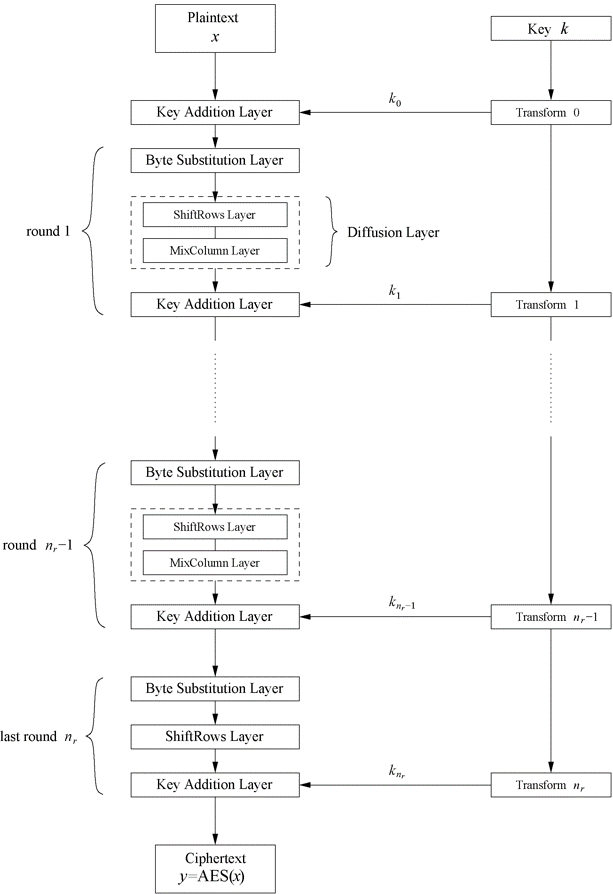
Rounds
Within each round of AES are different layers. The first iteration starts with a Key Addition Layer and then follows this pattern for the remaining rounds:
- Byte Substitution Layer
- ShiftRows Layer
- MixColumn Layer
- Key Addition Layer
The Byte Substitution layer acts as the confusion element, and the ShiftRows and MixColumn Layers act as the diffusion element. In the final round, the MixColumn layer is omitted.
We will now examine each layer separately.
Layers
- Byte Substitution Layer (S)
This layer consists of 16 identical S-box which take in 8 bits and output 8 bits. Let $ A_i $ be one byte of input. Then $ S(A_i)=B_i $
But what is the function S? First, the $ A_i^{-1} \in GF(2^8) $ is calculated. Then, an affine transformation is applied.
In software, S-boxes are usually a look up table.
References
Questions and comments
If you have any questions, comments, etc. please post them here.
Back to 2015 Summer Cryptography Paar