| Line 4: | Line 4: | ||
[[Category:cryptography]] | [[Category:cryptography]] | ||
| + | <center> <font size= 5> | ||
| + | ==[[2015_Summer_Cryptography_Paar|The Paar Lectures on Introductory Cryptography]]== | ||
| + | [http://slectures.projectrhea.org Slectures] by [[User:Agarwa65|Divya Agarwal]] and [[User:Khmarsh|Katie Marsh]] | ||
| + | </font size> | ||
| + | </center> | ||
| + | <center><font size= 4>2. Introduction to Cryptography</font size> | ||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
</center> | </center> | ||
---- | ---- | ||
Latest revision as of 11:03, 19 June 2015
Contents
The Paar Lectures on Introductory Cryptography
Slectures by Divya Agarwal and Katie Marsh
Introduction to cryptography
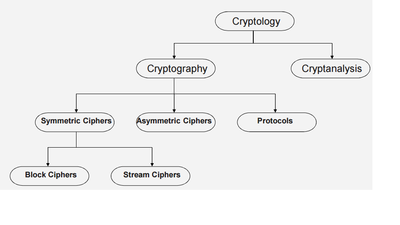
The block diagram below shows an overview of the field of cryptology.
Cryptography is the science of secret writing with the goal to hide the orginal message.
Cryptanalysis is the science and sometimes art of breaking cryptosystems.
Cryptography itself splits into three main branches:
1. Symmetric Algorithms :
- Also known as private-key, single-key or secret-key cryptography
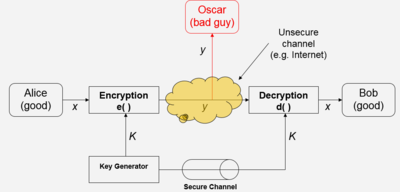
- In Fig 2, x is the plaintext message which Alice wants to send, y is the ciphertext message which has been encrypted, K is the key to encrypt or decrypt the message.
- Encryption equation : $ y = e_k(x) $ , where $ e_k(x) $ is the encryption function and,
- Decryption equation : $ x = d_k(y) $ , where $ d_k(x) $ is the decryption function
- Encryption and decryption are inverse operations if the same key K is used on both sides :
$ d_k(y)= d_k(e_k(x))= x $
- However, the system is only secure if an attacker does not learn the key K!
2. Asymmetric Algorithms :
- Also known as public-key cryptography.
- Unlike Symmetric cryptography, user possesses a secret key as well as a public key.
- We do not discuss this in detail in our slecture but use the references to learn more.
3. Cryptographic Protocols :
- Roughly speaking, crypto protocols deal with the application of cryptographic algorithms. More details in the reference book.
Conclusion
The main focus of slecture is on basics of cryptography uptil symmetric algorithms inlcuding understanding the maths behind it.
References
- C. Paar. Understanding Cryptography. Lecture Notes. Dept. of Electr. Eng. and Information Sciences, Ruhr University.
- C. Paar and J. Pelzl. Understanding Cryptography. A textbook for Student and Practitioners. Springer 2010.
Questions and comments
If you have any questions, comments, etc. please post them here.
Back to 2015 Summer Cryptography Paar